
Prof. Shaohua Wan
University of Electronic Science and Technology of China, China
 Open Access
Open Access
Article
Article ID: 99
by Muhammad Jaziem Mohamed Javeed, Azwaar Khan Azlim Khan, Nurul Hashimah Ahamed Hassain Malim
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
The prediction of drug-target interactions (DTIs) using machine learning techniques together with the proper representation of compounds can speed up the time-consuming experimental work in predicting DTIs especially when a large dataset is used. Hence, in this paper, we have proposed a new molecular descriptor based on LINGO Profiles known as LINGO Profiles Fingerprint (LPFP). LPFP is used together with machine learning to predict DTIs on a ChEMBL dataset. Dimensionality reduction using Association Rule Mining (ARM) is also introduced to overcome the high dimensionality suffered by LPFP. LPFP managed to reach an equal accuracy reading to the state-of-the-art descriptor called ECFP4 (Δ0.18%), but it suffers in the time taken (Δ27 mins) due to the dimensionality problem mentioned. Hence, three new smaller size LPFPs (s = 60%, s = 70%, s = 80%) were constructed by only extracting the important fragments using ARM and then a benchmark analysis with the original LPFP and ECFP4 fingerprints was done. This study not only solved the dimensionality problem, but also managed to excel in both the accuracy and time taken when predicting DTIs. An increase in the accuracy of over 250 times faster than the original LPFP was observed after the benchmark analysis is performed. Furthermore, an accuracy of over 80% was achieved in three new activity classes that are acquired from ChEMBL, further proving the promising performance of ARM which has made it favourable for LPFPs to be used in DTI prediction and in other drug discovery problems.
 Open Access
Open Access
Article
Article ID: 321
by Syed Raza Shah Gilani, Bahaudin Ghulam Mujtaba, Shehla Zahoor, Ali Mohammed AlMatrooshi
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
By the new century, the sheer complexity and number of reported cybercrime incidents had exposed major flaws in the cybersecurity infrastructure of industry giants, as well as governments. For example, there have been numerous attempts to intercept Google’s source code for the purposes of extracting confidential commercial data. National authorities were also slow to respond to the distribution of offensive images or copyrighted materials over the internet. While previous threats were mostly localized to certain computer systems, in particular countries, the emergence of the modern financial system has transformed digital crimes into a transnational phenomenon. In the intervening years, several companies, such as Lloyds in 2015, have been targets of financial hacking operations. The loss associated with cybercrime has been escalating annually, with figures indicating that costs borne by companies had quadrupled between the years of 2013 and 2015. The challenge has become worse in the recent years and artificial intelligence applications can create even more complexity and anxiety for professionals in every workplace. So, this trend of cybercrimes growing rapidly in the era of artificial intelligence is likely to affect developing and transnational economies, as more public and private sector banking institutions conduct their services online. Muslim countries must jointly collaborate, discuss, and link their spiritual principles to guard against, discourage, and prevent cybercrimes. Implications for Islamic nations along with their public and private sector leaders are explored in this manuscript.
 Open Access
Open Access
Article
Article ID: 383
by Gourab Basu, Kshanaprava Dhalsamant, Punyadarshini Punam Tripathy, Sonu Sharma
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
In this current research, the drying characteristics of carrot slices dried in a convective hot-air dryer are analyzed employing image analysis to determine the most significant factor. From the acquired images, nine parameters viz. redness (R), greenness (G), blueness (B), lightness (L), redness (a), yellowness (b), energy, entropy, and upper surface area of carrot slices were calculated using the algorithm developed in MATLAB 2015a. Boruta feature selection algorithm in the R console showed lightness, redness, and energy were the most significant features among calculated parameters. Additionally, single-layer feed-forward artificial neural network (ANN) architecture with three inputs (hot air temperature, thickness of slices, drying time), and outputs namely lightness, redness, and energy with one hidden layer was used to model input variables to that of responses. Multiple regression models are employed to optimize the drying condition by further assessing the behavior of response variables with hot air temperature and thickness of slices as inputs and lightness, redness, and energy as outputs. The lightness and redness of samples are found to be decreasing with an increase in temperature and a decrease in thickness. Whereas, the effect of these input parameters on energy, the measure of homogeneity of the product surface, is found to be reversed to that of the effect on lightness and redness. Lightness and redness are set to be highest, whereas energy was kept to be lowest. Convective hot air temperature of 60 ℃ and 7 mm thickness sample was found to provide the best quality product within the experiment range.
 Open Access
Open Access
Article
Article ID: 409
by Souad Bezzaoucha Rebai
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
In the following contribution, the control design of CPSs (Cyber Physical Systems) usually consists of an observer to estimate the state of the physical system and a controller to compute the control commands based on the state estimation studied. Our objective is to design control methods that are robust against attacks in the model, attenuating their effect and ensuring at the same time a reliable state and attack estimation allowing their detection and isolation while maintaining the system stability, integrity, and performance. The considered approach is based on the Lyapunov theory and LMI resolution approach in order to deduce the observers-controller gains. A robust output H∞ control and quadratic stabilization for nonlinear systems subject to actuator and sensor data deception attacks (cyber-physical-attacks) is proposed. The detection & identification issues are also reconsidered since the system states and the malicious signals will be reconstructed via a Polytopic-based T-S (Takagi-Sugeno) observer. An innovative design method where the attacked system is presented as an uncertain one subject to external disturbances is developed. A robust polytopic state feedback stabilizing controller based on a polytopic observer with disturbances attenuation for the resulting uncertain system is considered. To illustrate our proposed approach, we present a numerical example. An algorithm based on a robust polytopic controller ensuring asymptotic stability despite data deception attacks and external perturbations attenuation guaranteed by the H∞ norm will be given. Indeed, a PDC (Parallel Distributed Compensation) controller coupled with a polytopic observer to estimate the unmeasurable state variables and actuator/sensor attack signals will be designed for nonlinear systems subjected to data deception attacks.
 Open Access
Open Access
Review
Article ID: 100
by Nur Aqilah Paskhal Rostam, Nurul Hashimah Ahamed Hassain Malim, Nur Afzalina Azmee, Renato J. Figueiredo, Mohd Azam Osman, Rosni Abdullah
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
Ongoing research on the temporal and spatial distribution of algae ecological data has caused intricacies entailing incomprehensible data, model overfit, and inaccurate algal bloom prediction. Relevant scholars have integrated past historical data with machine learning (ML) and deep learning (DL) approaches to forecast the advent of harmful algal blooms (HAB) following successful data-driven techniques. As potential HAB outbreaks could be predicted through time-series forecasting (TSF) to gauge future events of interest, this research aimed to holistically review field-based complexities, influencing factors, and algal growth prediction trends and analyses with or without the time-series approach. It is deemed pivotal to examine algal growth factors for useful insights into the growth of algal blooms. Multiple open issues concerning indicator types and numbers, feature selection (FS) methods, ML and DL forms, and the time series-DL integration were duly highlighted. This algal growth prediction review corresponded to various (chronologically-sequenced) past studies with the algal ecology domain established as a reference directory. As a valuable resource for beginners to internalize the algae ecological informatics research patterns and scholars to optimize current prediction techniques, this study outlined the (i) aforementioned open issues with an end-to-end (E2E) evaluation process ranging from FS to predictive model performance and (ii) potential alternatives to bridge the literature gaps.
 Open Access
Open Access
Review
Article ID: 360
by Bojana Petrovic, Vesna Tunguz, Petr Bartos
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
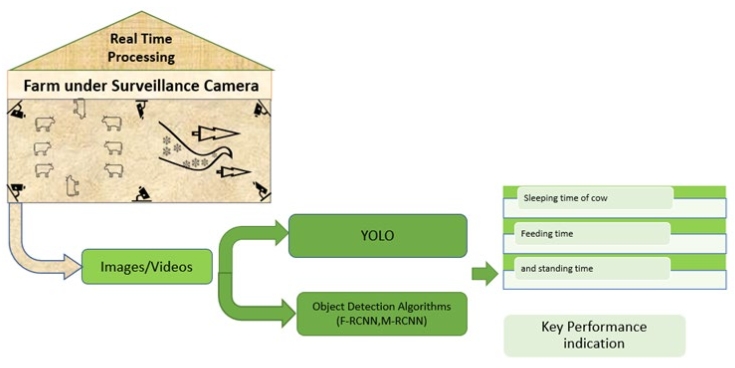
Nowadays, it is a challenge for farmers to produce healthier food for the world population and save land resources. Recently, the integration of computer vision technology in field and crop production ushered in a new era of innovation and efficiency. Computer vision, a subfield of artificial intelligence, leverages image and video analysis to extract meaningful information from visual data. In agriculture, this technology is being utilized for tasks ranging from disease detection and yield prediction to animal health monitoring and quality control. By employing various imaging techniques, such as drones, satellites, and specialized cameras, computer vision systems are able to assess the health and growth of crops and livestock with unprecedented accuracy. The review is divided into two parts: Livestock and Crop Production giving the overview of the application of computer vision applications within agriculture, highlighting its role in optimizing farming practices and enhancing agricultural productivity.
 Open Access
Open Access
Review
Article ID: 419
by Rakesh Roshan, Om Prakash Rishi, Mothukuri Sridevi
Computing and Artificial Intelligence, Vol.1, No.1, 2023;
Deep learning, a powerful subset of artificial intelligence, has emerged as a transformative force shaping the landscape of technology. This research delves into the multifaceted realm of deep learning, exploring its diverse applications, confronting inherent challenges, and envisioning future prospects that beckon innovation. The journey begins with a comprehensive examination of how deep learning has catalyzed breakthroughs in various domains. In the realm of applications, the study meticulously dissects the impact of deep learning on natural language processing (NLP), computer vision, autonomous systems, medical and healthcare domains, financial forecasting, and more. From deciphering human language nuances to revolutionizing medical diagnostics and propelling autonomous vehicles, deep learning’s applications redefine the possibilities of artificial intelligence. As the exploration of applications and challenges unfolds, the research pivots towards the future horizons of deep learning. It contemplates the trajectory of explainable AI (XAI), the promises held by transfer learning, the integration of deep learning with quantum computing and neuromorphic architectures, and the ethical dimensions that will shape the evolution of AI for the greater good. The abstract encapsulates a panoramic view of “Deep Insight”, where deep learning transcends its current achievements, confronting challenges head-on and embracing a future characterized by responsible innovation. This research invites stakeholders, researchers, and enthusiasts to embark on a journey of exploration, discovery, and contemplation, as the realm of deep learning continues to unfold its vast and captivating horizons.