Development of a stacked hybrid Decision Tree model leveraging the NSL-KDD dataset
Abstract
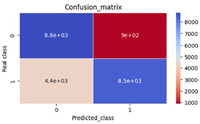
Intrusion detection in information technology as well as operational technology networks is highly required in modern day systems due to the increased spate of cyber-attacks in both number and complexity. Anomaly-based intrusion detection systems which have the capacity to detect novel or zero-day attacks are highly employed in this regard. One important component of anomaly-based intrusion detection systems which ensures their behaviour is artificial intelligence in general and machine learning in particular. The burden in modern day cybersecurity research is to investigate and develop models that can outperform existing ones. This paper is aimed at developing a hybrid decision tree model using the stacking ensemble approach. Performances were measured on the basis of recall, precision, accuracy, F1-score, receiver operating characteristics and confusion matrices. The hybrid model presented a precision of 97%, accuracy of 81%, F1-score of 80% and AUC score of 0.96, respectively.
References
[1]Mohajan HK. Third industrial revolution brings global development. Journal of Social Sciences and Humanities 2021; 7(4): 239–251.
[2]Orukpe PE, Erhiaguna TO, Agbontaen FO. Computer security and privacy in wireless local area network in Nigeria. International Journal of Engineering Research in Africa 2013; 9: 23–33. doi: 10.4028/www.scientific.net/jera.9.23
[3]Shruti M. Types of cyber attacks you should be aware of in 2023. Available online: https://www.simplilearn.com/tutorials/cyber-security-tutorial/types-of-cyber-attacks (accessed on 11 August 2023).
[4]FORTINET. Types of cyber attacks. Available online: https://www.fortinet.com/resources/cyberglossary/types-of-cyber-attacks (accessed on 11 August 2023).
[5]DNV. The three-pillar approach to cyber security: Data and information protection. Available online: https://www.dnv.com/article/the-three-pillar-approach-to-cyber-security-data-and-information-protection-165683 (accessed on 11 August 2023).
[6]James K. What are the 5 pillars of cybersecurity? Available online: https://cybersecurityforme.com/what-are-the-5-pillars-of-cybersecurity (accessed on 11 August 2023).
[7]Osa E. Cyber security terminologies and concepts. In: SMART-IEEE-ACity-ICTU-CRACC-ICTU-Foundations Series Book Chapter on Web of Deceit. Creative Research Publishers; 2022. pp. 231–236.
[8]Rama Devi R, Abualkibash M. Intrusion detection system classification using different machine learning algorithms on KDD-99 and NSL-KDD datasets—A review paper. International Journal of Computer Science and Information Technology 2019; 11(3): 65–80. doi: 10.5121/ijcsit.2019.11306
[9]Abuh A, Orukpe PE. Development of an integrated campus security alerting and access control system. In: Emerging Trends in Engineering Research and Technology Vol. 9. Book Publisher International; 2020. pp. 57–67.
[10]Chudasma P. Network Intrusion Detection System using Classification Techniques in Machine Learning [Master’s thesis]. Dublin Business School; 2020.
[11]Sangfor Technologies. What is an intrusion detection system and how does it work. Available online: https://www.sangfor.com/glossary/cybersecurity/what-is-intrusion-detection-system-and-how-does-it-work (accessed on 11 August 2023).
[12]Velimirovic A. What is an intrusion detection system? Available online: https://phoenixnap.com/blog/intrusion-detection-system (accessed on 11 August 2023).
[13]FORTINET. Intrusion Detection System (IDS). Available online: https://www.fortinet.com/resources/cyberglossary/intrusion-detection-system (accessed on 11 August 2023).
[14]Géron A. Hands-on Machine Learning with Scikit-Learn, Keras, and TensorFlow. O’Reilly Media, Inc.; 2019.
[15]Alladi SK. Effectively Improving the Efficiency and Performance of an Intrusion Detection System Using Hybrid Machine Learning Models [Master’s thesis]. National College of Ireland; 2020.
[16]Sapre S, Ahmadi P, Islam K. A robust comparison of the KDDCup99 and NSL-KDD IoT network intrusion detection datasets through various machine learning algorithms. arXiv 2019; arXiv:1912.13204. doi: 10.48550/arXiv.1912.13204
[17]Vinayakumar R, Alazab M, Soman KP, et al. Deep learning approach for intelligent intrusion detection system. IEEE Access 2019; 7: 41525–41550. doi: 10.1109/access.2019.2895334
[18]Li Y, Gao J, Li Q, Fan W. Ensemble learning. In: Data Classification Algorithms and Applications’ Data Mining and Knowledge Discovery Series. CRC Press; 2015. pp. 498–500.
[19]Bhandari A. Guide to AUC ROC Curve in machine learning: What is specificity? Available online: www.analyticsvidhya.com/blog/2020/06/auc-roc-curve-machine-learning/ (accessed on 8 June 2023).
Copyright (c) 2023 Edosa Osa, Patience Orukpe, Iruansi Usiholo

This work is licensed under a Creative Commons Attribution 4.0 International License.